SHA2 IP Core Datasheet

Core Facts |
|
|
Provided with Core |
|
|
Documentation |
User Guide, Design Guide |
|
Design File Formats |
Encrypted File |
|
Instantiation Templates |
VHDL |
|
Reference Designs & Application Notes |
Vivado Project, See Reference design manual |
|
Additional Items |
Demo on KCU116 |
|
Support |
|
|
Support Provided by Design Gateway Co., Ltd. |
|
Design Gateway Co., Ltd.
E-mail: ip-sales@design-gateway.com
URL: design-gateway.com
Features
· Supports SHA-224, SHA-256, SHA-384, SHA-512, SHA-512/224, and SHA-512/256 algorithms.
· Accepts input message lengths up to 264–8 bits (SHA-224/256) and 2128–8 bits (SHA-384/512)
· High-performance architecture with only:
· 65 cycles per 64-byte block for SHA-224/256.
· 81 cycles per 128-byte block for SHA-384/512.
· Achieves throughput up to:
· 1.969 Gbps @ 250 MHz for SHA-256
· 3.160 Gbps @ 250 MHz for SHA-512
· User data interface: Utilizes a 32-bit AXI4 stream interface.
Table 1 Example Implementation Statistics for SHA2-IP
|
Family |
Example Device |
Fmax (MHz)
|
CLB Regs
|
CLB LUTs
|
CLB1 |
IOB |
BRAMTile |
Design Tools |
|
Kintex-UltraScale+ |
xcku5p-ffvb676-2-e |
250 |
1905 |
3581 |
650 |
- |
- |
Vivado 2022.1 |
Notes:
1) The actual logic resource depends on the percentage of unrelated logic.
Figure 1 SHA2 Block Diagram
General Description
The SHA2 IP is proved algorithmic reliability and functional correctness by passing example SHA Test Vectors for Hashing Byte-Oriented Messages, including both long and short message cases.
For reference, see: https://csrc.nist.gov/projects/cryptographic-algorithm-validation-program/secure-hashing
Functional Description
The SHA2 IP core allows users to easily implement various SHA2 hash algorithms. Users interact with the core via control signals to configure the algorithm, input data, and manage the hash output. Table 2 shows SHA2-IP parameters. Table 3 shows interface signals of SHA2-IP.
Table 2 IP Core Parameters
|
Parameter name |
Value |
Description |
|
USE_RAM |
0-1 |
Enable use of block RAM buffer. Default: 0 1 – Use block RAM size 4KB buffer. |
|
USE_STREAM_OUT |
0-1 |
Enable hash output stream. Default: 1 1 – Enable hash output stream. |
Table 3 Interface signals
|
Signal name |
Dir |
Description |
|
RstB |
In |
IP core system reset. Active low. |
|
Clk |
In |
IP core system clock. |
|
version[31:0] |
Out |
32-bit version number of IP. |
|
Stream DataIn Control |
||
|
SHAInReady |
Out |
Asserted to ‘1’ when the SHA2-IP is ready to accept SHAInData. |
|
SHAInCMD[2:0] |
In |
Selects the SHA2 algorithm to be
used: |
|
SHAInValid |
In |
Asserted to ‘1’ to indicate that SHAInData is valid. |
|
SHAInLast |
In |
Asserted to ‘1’ to indicate the last word of input data. During this cycle, SHAInKeep must be used to specify valid bytes. |
|
SHAInKeep[3:0]* |
In |
Byte enable of SHAInData. Valid when SHAInValid=‘1’. During packet transmission, this signal is equal to “1111” for enabling all 32-bit data except the final data of the packet which can be equal to four values: “0001”, “0011”, “0111”, or “1111” when SHAInData[7:0], [15:0], [23:0], or [31:0] is valid respectively. |
|
SHAInData[31:0] |
In |
Input data to be processed by the SHA2-IP. |
|
HashOut Control |
||
|
HashOutValid |
Out |
Asserted to ‘1’ to indicate the output hash is valid. |
|
HashOut224[223:0] |
Out |
Hash output for SHA-224 when HashOutValid=‘1’ and SHAInCMD[2:0]=“010”. |
|
HashOut256[255:0] |
Out |
Hash output for SHA-256 when HashOutValid=‘1’ and SHAInCMD[2:0]=“011”. |
|
HashOut384[383:0] |
Out |
Hash output for SHA-384 when HashOutValid=‘1’ and SHAInCMD[2:0]=“100”. |
|
HashOut512[511:0] |
Out |
Hash output for SHA-512 when HashOutValid=‘1’ and SHAInCMD[2:0]=“101”. |
|
HashOut512_224[223:0] |
Out |
Hash output for SHA-512/224 when
HashOutValid=‘1’ and |
|
HashOut512_256[255:0] |
Out |
Hash output for SHA-512/256 when
HashOutValid=‘1’ and |
|
Signal name |
Dir |
Description |
|
Stream HashOut Control** |
||
|
SHAOutReady |
In |
Indicates when the hash output is ready to be read. |
|
SHAOutValid |
Out |
Asserted to ‘1’ to indicate the output hash is valid. |
|
SHAOutLast |
Out |
Asserted to ‘1’ to indicate that this is the last output data word. |
|
SHAOutData[31:0] |
Out |
Hash output data stream. |
Note:
* To hash an empty message, assert SHAInValid and SHAInLast to ‘1’, and set SHAInKeep to “0000”.
** USE_STREAM_OUT must be set to 1 to enable stream hash output.
Additionally, users may refer to the SHA2-IP reference design documents for example implementations, which provides a clearer understanding of how to utilize the SHA2-IP.
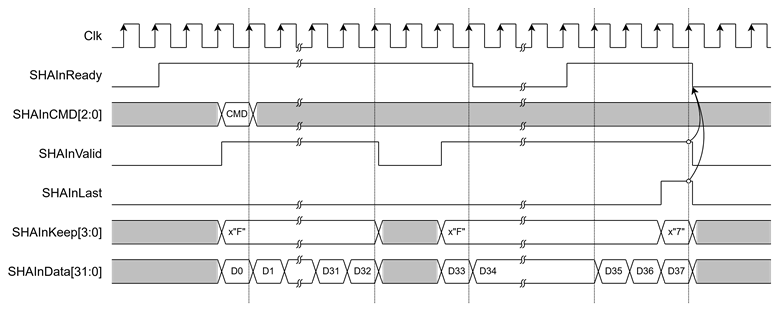
Figure 2 Example Timing Diagram of Data Transmission
SHA2-IP operation is as simple as 2 steps as below and Figure 2 shows timing diagram of SHA256IP interface signals.
· Data control
Before sending any data, the user must specify the desired SHA2 algorithm by setting SHAInCMD[2:0]. This value must be valid on the first clock cycle of the input data stream. The selected algorithm will be used throughout the entire hash operation.
To initiate data transfer, the user must assert SHAInValid to ‘1’ along with valid data on SHAInData[31:0]. Data will be accepted by the SHA2-IP only when SHAInReady is ‘1’. If SHAInReady is ‘0’, the user must hold all inputs steady until SHAInReady returns to ‘1’.
During data transfer, SHAInKeep must be set to “1111” to indicate that all 4 bytes of SHAInData are valid, except on the final word of the message. To mark the final word, the user must assert SHAInLast to ‘1’ and set SHAInKeep to reflect the number of valid bytes (e.g., “0001”, “0011”, “0111”, or “1111”).
After SHAInLast is asserted, SHAInReady will de-assert to ‘0’ in the next clock cycle, indicating that the SHA2-IP is now performing hash computation and will not accept new input until the operation is complete.
· Hash output
After the user sends the final input word with SHAInLast asserted, the SHA2-IP begins hash computation. When the operation is complete, HashOutValid is asserted to ‘1’ to indicate that the hash result is ready. The output hash will be presented on one of the dedicated hash output ports, depending on the algorithm selected via SHAInCMD[2:0].
· If SHAInCMD = "010", the result is on HashOut224.
· If SHAInCMD = "011", the result is on HashOut256.
· If SHAInCMD = "100", the result is on HashOut384.
· If SHAInCMD = "101", the result is on HashOut512.
· If SHAInCMD = "110", the result is on HashOut512_224.
· If SHAInCMD = "111", the result is on HashOut512_256.
SHAInReady will be reasserted to ‘1’ in the next cycle, indicating that the SHA2-IP is ready to accept new input data.
· Stream Hash output
The SHA2-IP supports streaming of hash output through a 32-bit data bus. Once the hash computation is complete, SHAOutValid will assert to ‘1’, and SHAOutData[31:0] will contain the valid hash result. To receive the hash output, the user must assert SHAOutReady to ‘1’. If SHAOutReady is ‘0’, the hash output will be held, and SHAOutData[31:0] will not be updated until SHAOutReady is asserted again.
When the final word of the hash is valid, SHAOutLast will assert to ‘1’ to indicate the end of the output stream.
If the user does not intend to use the stream hash output, the user must either always set SHAOutReady to ‘1’ or disable the stream output by setting USE_STREAM_OUT to ‘0’.
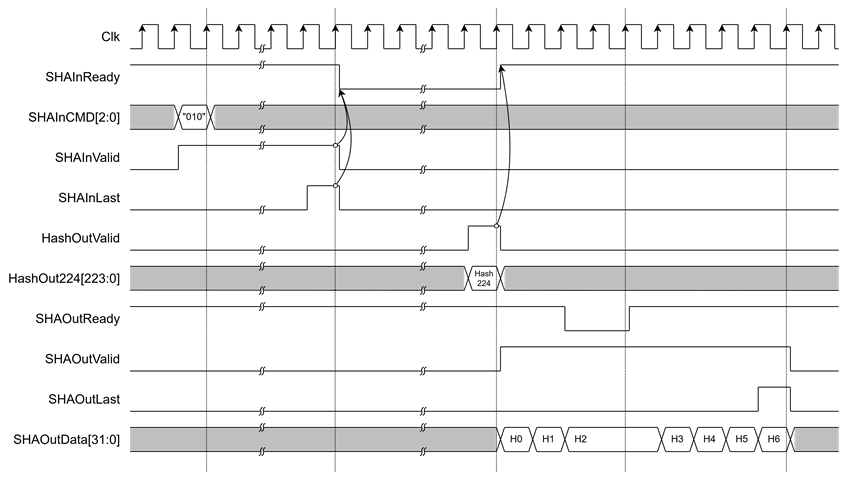
Figure 3 Example Timing Diagram of SHA-224 Hash Output
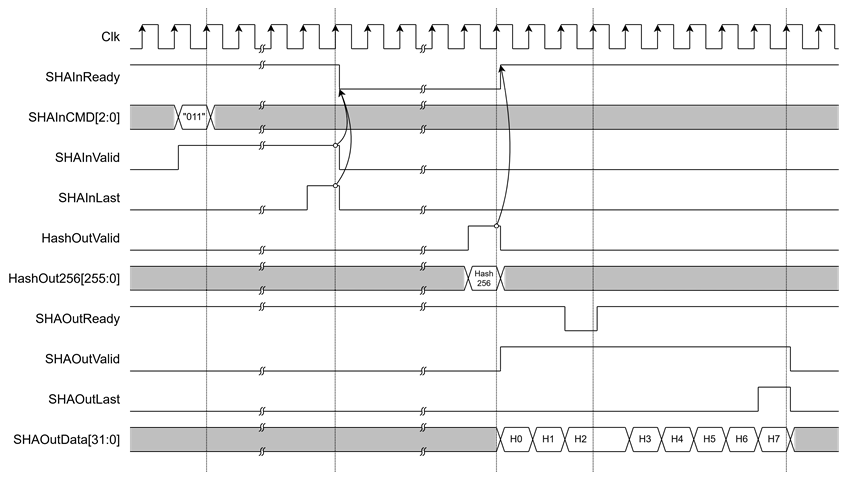
Figure 4 Example Timing Diagram of SHA-256 Hash Output
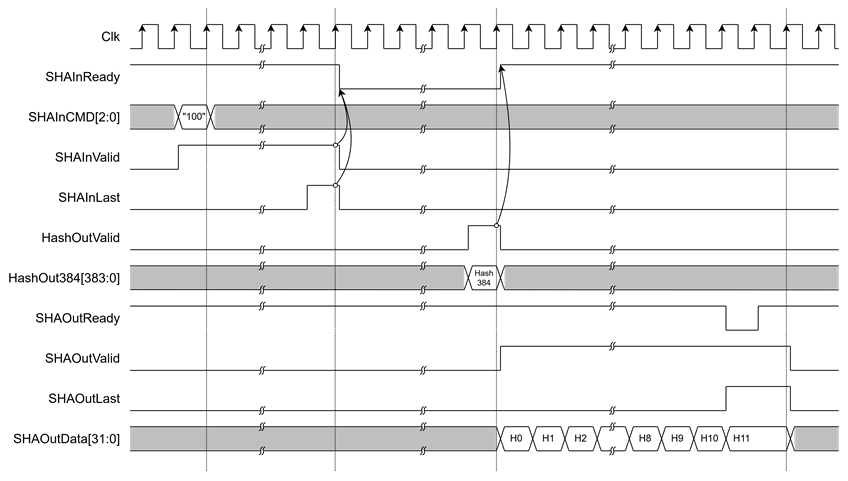
Figure 5 Example Timing Diagram of SHA-384 Hash Output
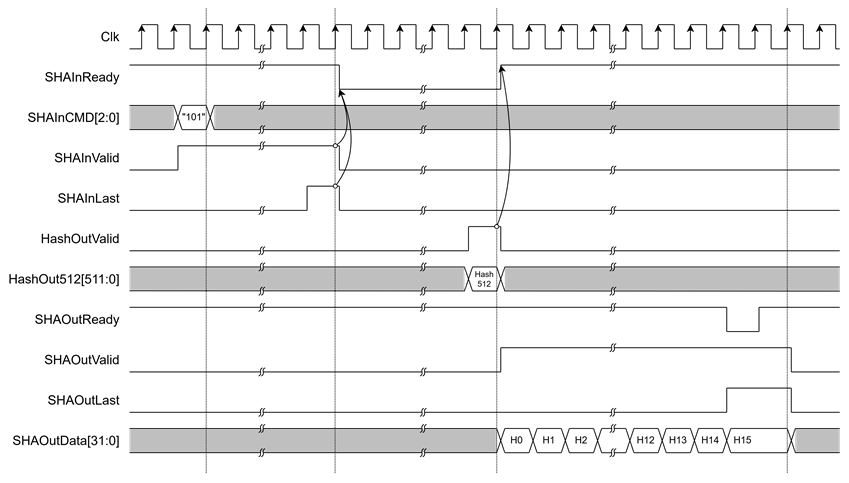
Figure 6 Example Timing Diagram of SHA-512 Hash Output
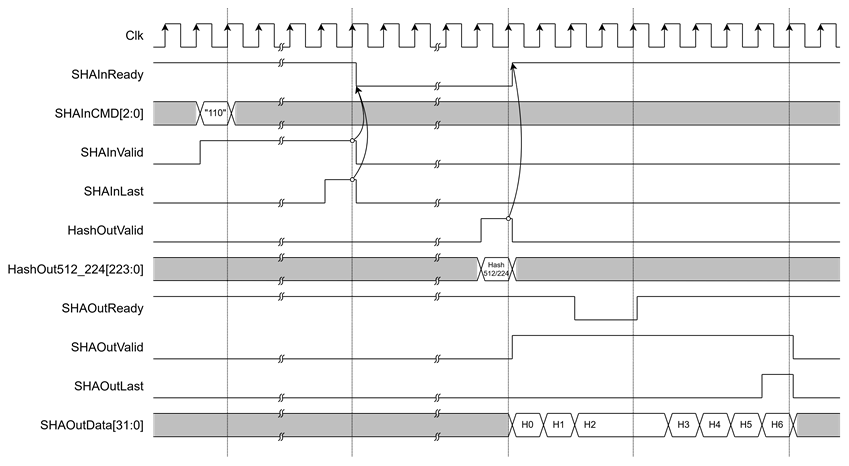
Figure 7 Example Timing Diagram of SHA-512/224 Hash Output
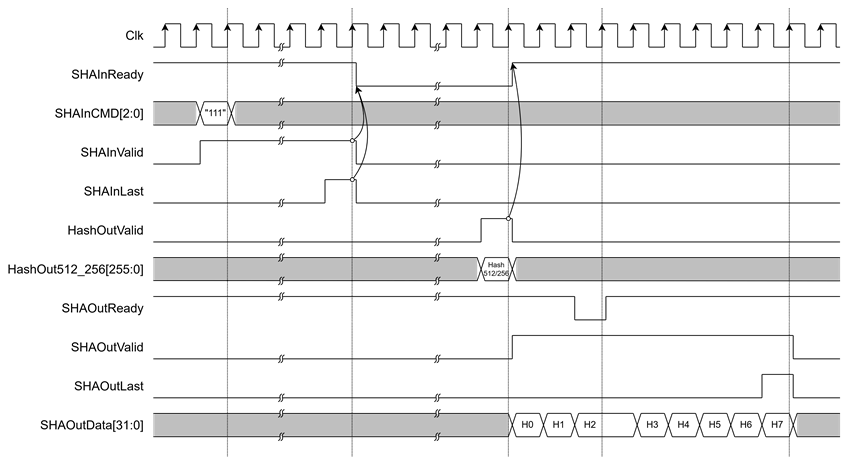
Figure 8 Example Timing Diagram of SHA-512/256 Hash Output
Verification Methods
The SHA2 IP Core functionality was verified on real board design by using KCU116 development board.
Recommended Design Experience
The user must be familiar with HDL design methodology to integrate this IP into a system.
Ordering Information
This product is available directly from Design Gateway Co., Ltd. Please contact Design Gateway Co., Ltd. For pricing and additional information about this product, use the contact information on the front page of this datasheet.
Revision History
|
Revision |
Date (D-M-Y) |
Description |
|
1.00 |
22-Apr-25 |
Initial release |
